Threat intelligence enriched with External Attack Surface Management, Brand Protection, and Dark Web Radar.
Protect your business from the dangers lurking in the hidden corners of the internet.
Effective threat hunting and threat actor tracking with behavioral analytics.
Discover your assets with a hacker mindset.
Stay ahead of threat actors with actionable intelligence alerts.
Evaluate the security posture of your entire supply network.
Your guide in harnessing the full potential of our platform.
Hear SOCRadar’s impressive achievements from our clients.
Automate and operationalize your security operations.
Consulting and professional services for cybersecurity excellence.
Industry, sector, and region-based in-depth research.
Discover the heartbeat of cyberspace through a collection showcasing the latest incidents.
Discover how XTI empowers organizations to proactively identify, mitigate, and respond to evolving cyber threats.
Register for our live webinars, and watch our on-demand webinars instantly.
Dive deep into the world of cyber threats, advanced analysis techniques, and cutting-edge strategies.
Stay informed and up-to-date on the latest cybersecurity trends.
Explore SOCRadar’s learning experience to fuel your cybersecurity journey with insights that exceed industry standards.
We offer expert-led, and exclusive trainings to help you master the latest in cybersecurity, trusted by over 2,000 top companies.
Scan the dark web to prevent your leaks from turning into real risks.
Instantly access dark web findings about your organization’s assets.
Check if there is anything about you in SOCRadar’s ever-expanding breach database.
Track threat actors and groups by country or industry for effective follow-up.
Explore threat actors’ tactics, techniques, activities, and detailed profiles targeting your industry or region.
All-in-one next-generation tools for investigating everyday events like phishing, malware, account breach, etc.
Power your search with SOCRadar’s IOC Radar.
Let’s get to know each other better.
Broaden your market reach and increase ARR with SOCRadar Extended Threat Intelligence.
Get informed of our upcoming events.
Latest news about our platform, company, and what’s being said about us.
Begin an extraordinary journey in your professional path with SOCRadar.
We’d like to hear from you.
SOCRadar Training Series – Mastering AI in Cybersecurity From Theory to Practice
Resources
[Update] October 23, 2024: “Founder of Just Evil and KillNet Allegedly Killed in Drone Attack”
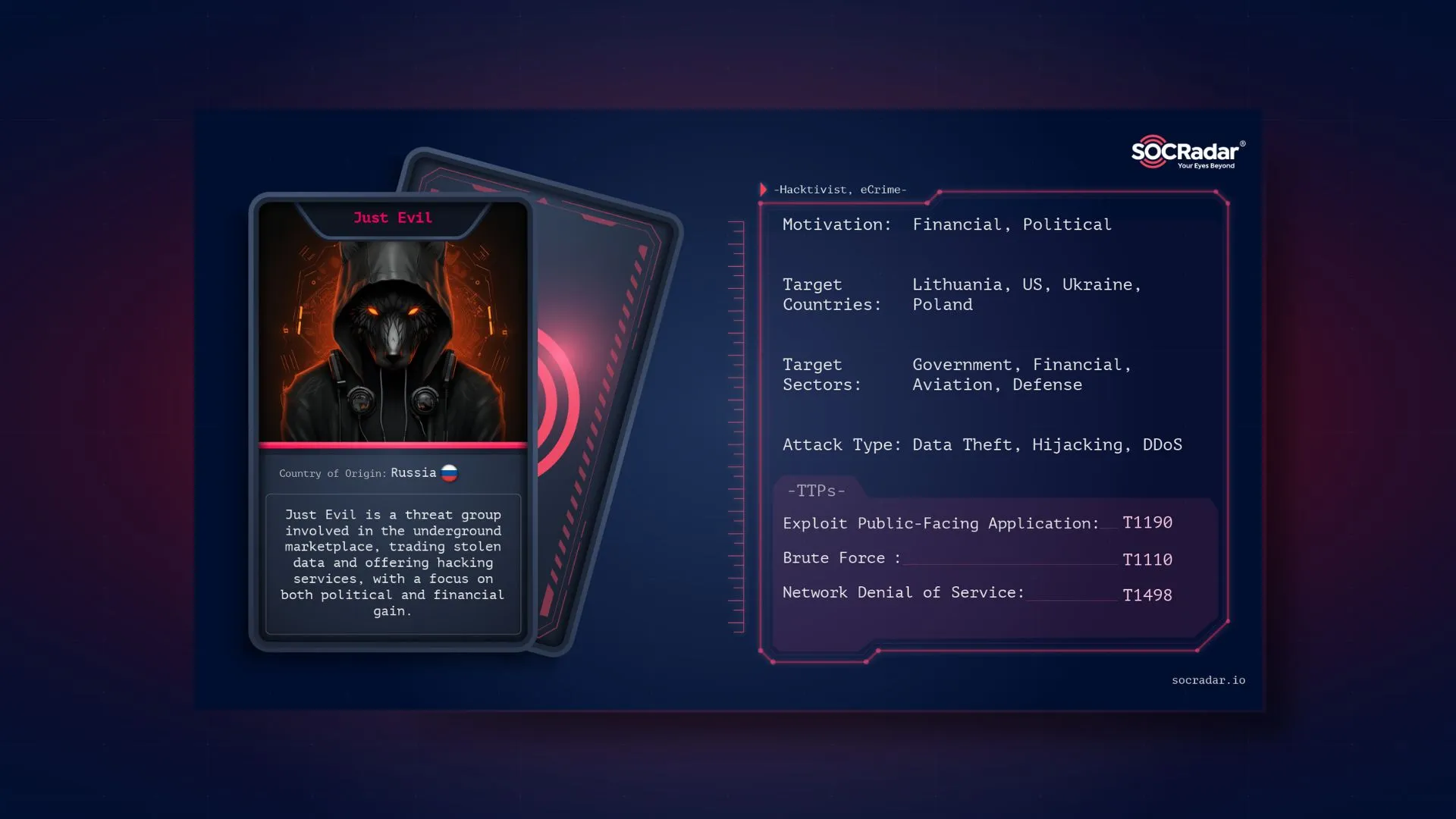
Just Evil is a pro-Russian cyber threat group formed in January 2024 by KillMilk. This group emerged following internal changes within KillNet, particularly regarding its sale to another owner and shift towards commercial motivations under the leadership of Deanon Club. Just Evil, like KillNet 2.0, is focused on maintaining an ideological mission, distancing itself from financial(!) motives to retain influence in the pro-Russian hacktivist landscape.
Just Evil’s Telegram logo
Short answer is KillMilk, ex-leader of KillNet. The original KillNet, widely known for its hacktivist operations, sold its primary Telegram channel to Deanon Club. This transaction marked a significant turning point, as Deanon Club shifted the group toward more commercial activities.
Threat actor card for Just Evil
Dissociating from this commercialization, KillMilk established Just Evil to maintain an ideological stance in the pro-Russian cyber community. At the same time, KillNet 2.0 another pro-Russian group was formed as a decentralized collective focused on non-commercialized, ideological missions, further fragmenting the pro-Russian cyber landscape.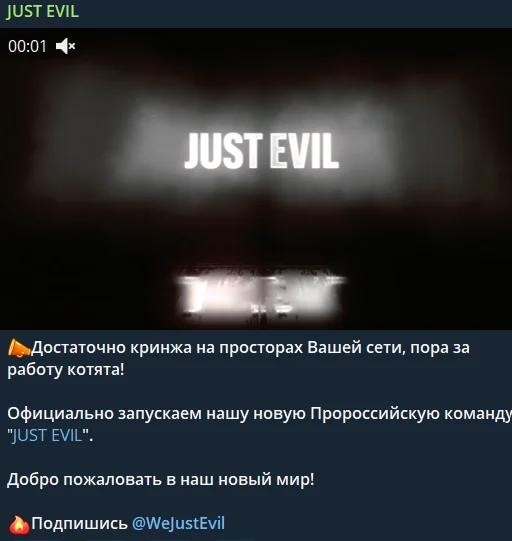
Announcement post of Just Evil in January 31, 2024
However, the above description may lead to just another question.
KillMilk is a key figure in the pro-Russian cyber landscape, best known for leading the hacktivist group KillNet. Initially, he was seen as the driving force behind the group’s operations, which were heavily focused on supporting Russian geopolitical interests, particularly during the Russia-Ukraine war. Under his leadership, KillNet launched a series of high-profile DDoS attacks against Western entities, positioning itself as a prominent pro-Russian hacktivist group.
Dark Web Profile: KillNet
However, by early 2024, cracks begin to show in KillMilk’s leadership. Internal tensions arose, with several members of KillNet publicly accusing him of unethical actions and a lack of technical expertise, which they felt undermined the group’s credibility. These criticisms were further amplified when Russian news outlet Gazeta.ru identified KillMilk as being linked to Nikolai Nikolaevich Serafimov, a controversial figure with a questionable background, adding to the group’s internal discord.
Amidst this growing dissent, KillMilk decided to step down from his leadership role, handing control of KillNet over to Deanon Club. This transition marked a turning point for KillNet, as Deanon Club began steering the group away from its original hacktivist, patriotic mission toward a more financially motivated agenda. Before his departure, KillMilk had overseen some of KillNet’s largest-scale operations, including DDoS attacks on major targets such as Microsoft’s Azure, Outlook, and OneDrive.
For further information about Deanon Club and KillNet check out our relevant blog post: Beyond Hacktivism: Deanon Club, KillNet, and the Russian Dark Web Market Wars
Furthermore, in addition to these attacks, KillNet also attempted to expand its influence by forming a subsidiary group called KillNet Palestine during the Israel-Hamas conflict. However, due to the internal struggles within KillNet, the group was probably unable to play a significant role in the conflict. Despite this, one of KillNet’s close allies, Anonymous Sudan, remained active and continued to collaborate with pro-Russian cyber actors for some time. However now Anonymous Sudan is also defunct.
Following KillMilk’s exit, the fate of KillNet shifted dramatically. While the group retained its name, Deanon Club emerged as the primary force behind its activities. So, were these splits and changes in names and groups just about motivations?
We just discussed their intention to distance themselves from financial motives, but, as always, human nature finds it hard to resist greed.
Just Evil’s launch of Just Market raises questions about their ideological stance, which claims to distance itself from financial motivations. Despite positioning themselves as a group with decentralized, anti-commercial goals, their first market post directly contradicts this claim. Offering services like GMail access, cryptocurrency laundering, document forgery, and security auditing, Just Market appears to cater to cybercrime for profit.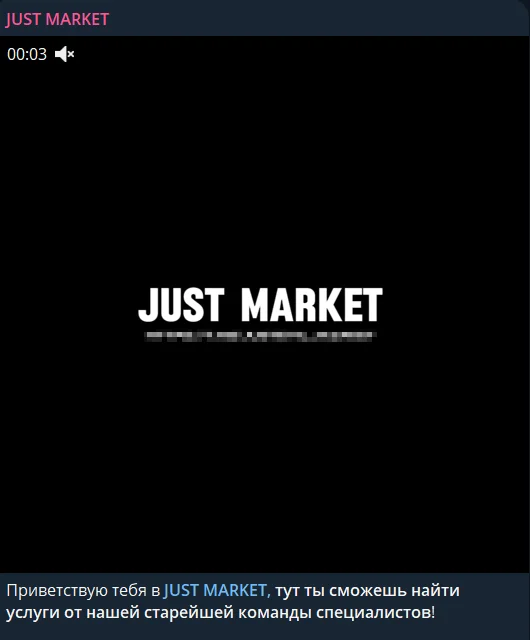
Just Market launched in April of 2024
While Just Evil emphasizes that they don’t operate destructively within Russia, this limitation does little to align with their proclaimed ideological mission. Instead, it suggests a pragmatic approach to avoiding local repercussions while still engaging in illegal activities globally.
Just Evil employs a variety of tactics and techniques that align with its mission of supporting Russian geopolitical interests. The group’s operations are specifically designed to target nations and organizations considered adversaries to Russia, with a strong emphasis on Western countries, NATO members, and Ukraine.
One of the primary tactics used by Just Evil is Distributed Denial of Service (DDoS) attacks. These attacks overwhelm target systems with a flood of internet traffic, causing significant disruptions to online services and operations in the targeted nations. This method of attack is intended to cripple the digital infrastructure of countries seen as enemies.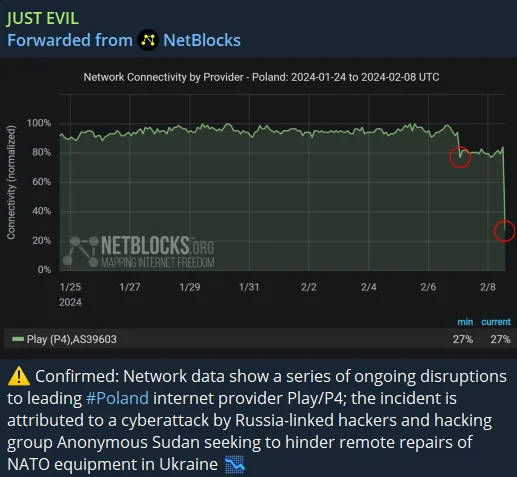
Attack on Polish internet provider
Another notable tactic is website defacement. Just Evil frequently defaces websites to publicly shame and spread propaganda against Western governments and organizations. This approach not only damages the reputation of the targets but also serves to disseminate anti-Western messages and propaganda.
Data breaches are also a key component of Just Evil’s strategy. By infiltrating and stealing sensitive information, the group aims to make this data public or use it strategically. This can involve blackmail, espionage, or other forms of strategic manipulation, further destabilizing the security and operational integrity of their adversaries.
While KillMilk led the KillNet group, most threats involved DDoS attacks. However, as Just Evil under KillMilk’s leadership and with the new(?) team, their tactics have shifted toward more destructive methods, including leaking classified data and gaining initial access to critical industries.
In terms of leadership, Just Evil is spearheaded by KillMilk, a prominent figure from the original KillNet operations. His leadership continues to guide the group’s activities and strategic objectives, ensuring that their operations remain focused on their ideological goals.
The motivation behind Just Evil’s actions is deeply rooted in pro-Russian geopolitical objectives. The group’s primary aim is to disrupt and undermine Western governments and institutions, thereby aligning its operations with broader Russian interests.
The Just Evil team, led by KillMilk, has consistently targeted NATO and its allied nations, though Ukraine has not been a significant focus since the Just Evil launch. Lithuania is their most frequent target. The graphic below illustrates the unique posts aimed at specific countries and their organizations, though some numbers may reflect the same attack with varied outcomes or follow-ups.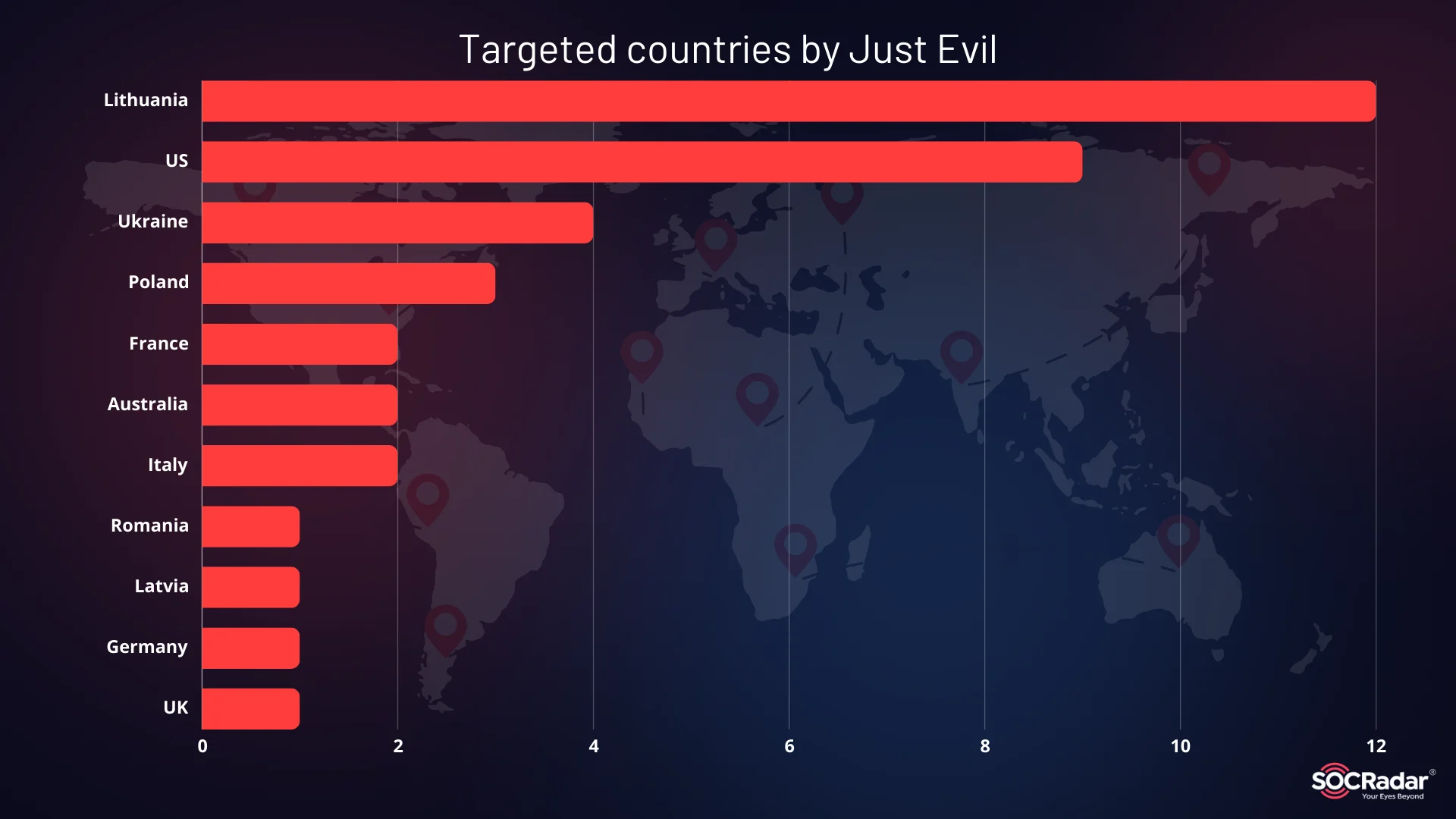
Targets specified in their Telegram channel
Once again, the US is a key target, along with countries that closely align with Lithuania. The rest of the list indicates that their actions align with Russia’s strategic interests.
Just Evil represents an evolution in the pro-Russian cyber landscape, emerging as a key player with ideological roots, though not completely immune to financial motivations, as seen with the launch of Just Market. While the group seeks to distance itself from the commercial activities that defined KillNet’s later phase under Deanon Club, its actions suggest a blend of hacktivism and pragmatic cybercrime.
Just Evil’s operations, including DDoS attacks, website defacements, and data breaches, are primarily aimed at Western nations and NATO members, aligning with Russia’s geopolitical goals. However, the contradictions in their actions and stated motivations leave room for speculation about the true nature of the group’s objectives.
SOCRadar’s advanced threat intelligence capabilities can provide critical insights into groups like Just Evil by monitoring dark web channels and forums, where Just Evil operates and promotes illegal services. SOCRadar’s Dark Web Monitoring can track discussions, data leaks, and market activities associated with Just Evil, allowing organizations to stay ahead of potential threats. Moreover, Attack Surface Management features offer proactive vulnerability assessments, while Threat Actor Intelligence service helps defend against the exact tactics employed by Just Evil. SOCRadar provides a comprehensive suite of tools to mitigate risks from this evolving threat actor, ensuring organizations can safeguard their assets and operations effectively.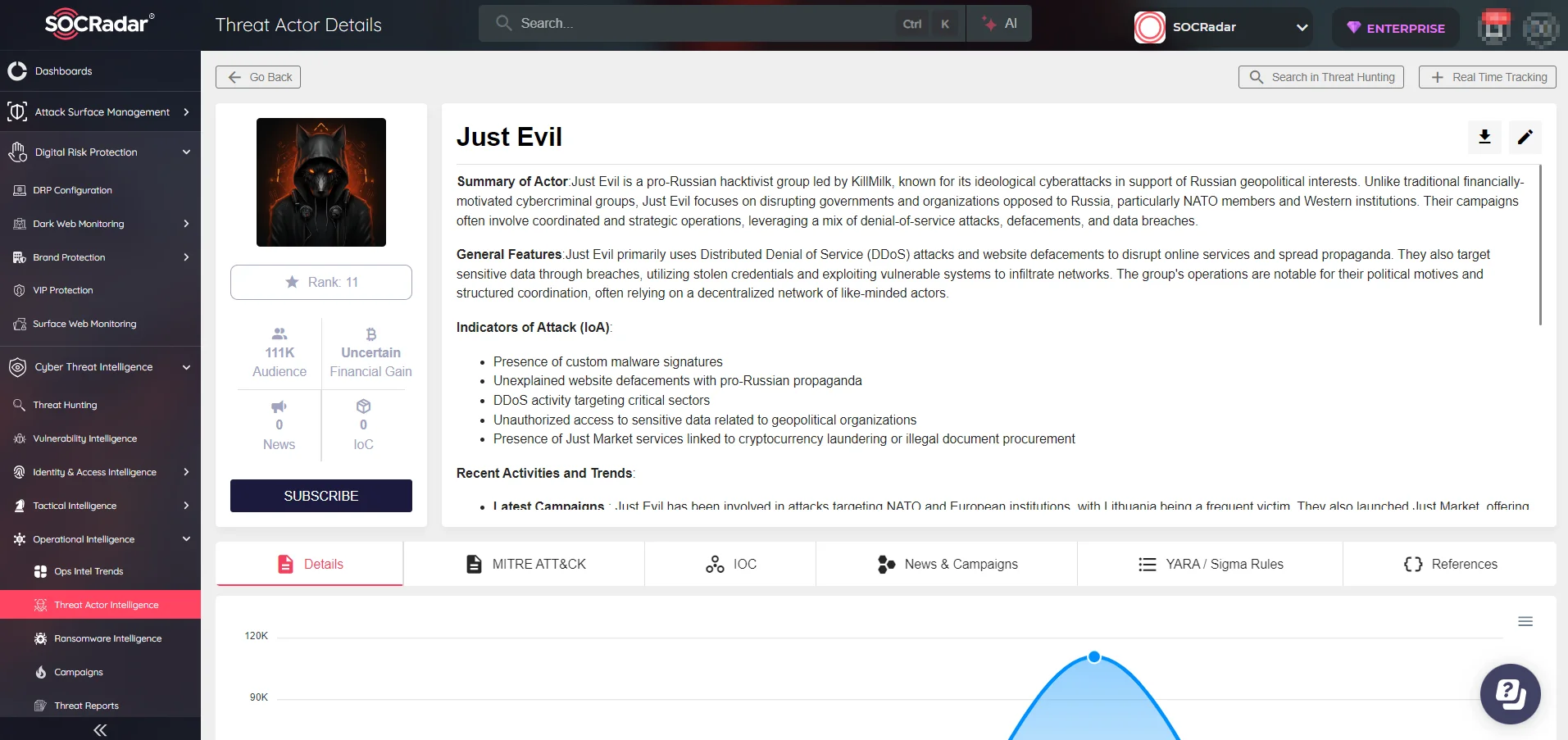
SOCRadar’s Threat Actor Intelligence
To defend against Just Evil’s diverse range of tactics, it’s crucial to adopt a multi-layered approach that encompasses both proactive and reactive measures. Here’s how organizations can mitigate their attacks:
Additionally, organizations can also check their domain’s DoS Resilience for free in SOCRadar Labs.
A recent message shared on the Just Evil channel claims that KillMilk, the founder of KillNet and Just Evil, has reportedly died in a Ukrainian UAV attack. The message, forwarded from the Russian group UserSec, describes the circumstances of the attack, suggesting a fuel explosion caused by the drone strike. While this raises speculation about an information operation, it follows KillMilk’s recent threats against the US government and a prominent cybersecurity researcher. Additionally, Just Evil’s channel has been renamed to “DEAD.” However, there is no concrete evidence to support the claim, and the image shared below appears to be an old photo.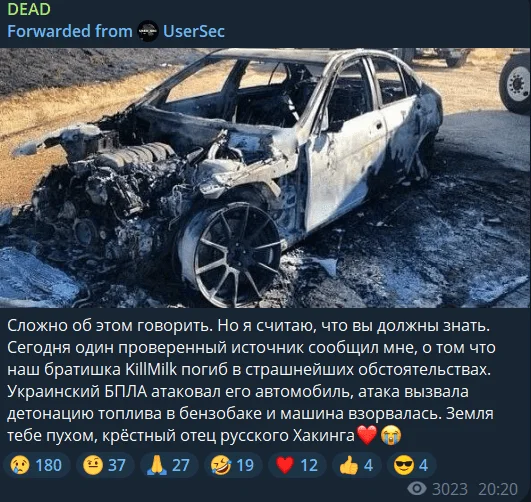
The Telegram post from the Just Evil group, now renamed to “DEAD,” shared a message claiming that KillMilk has died following a UAV attack.
Subscribe to our newsletter and stay updated on the latest insights!
PROTECTION OF PERSONAL DATA COOKIE POLICY FOR THE INTERNET SITE
Protecting your personal data is one of the core principles of our organization, SOCRadar, which operates the internet site (www.socradar.com). This Cookie Usage Policy (“Policy”) explains the types of cookies used and the conditions under which they are used to all website visitors and users.
Cookies are small text files stored on your computer or mobile device by the websites you visit.
Cookies are commonly used to provide you with a personalized experience while using a website, enhance the services offered, and improve your overall browsing experience, contributing to ease of use while navigating a website. If you prefer not to use cookies, you can delete or block them through your browser settings. However, please be aware that this may affect your usage of our website. Unless you change your cookie settings in your browser, we will assume that you accept the use of cookies on this site.
1. WHAT KIND OF DATA IS PROCESSED IN COOKIES?
Cookies on websites collect data related to your browsing and usage preferences on the device you use to visit the site, depending on their type. This data includes information about the pages you access, the services and products you explore, your preferred language choice, and other preferences.
2. WHAT ARE COOKIES AND WHAT ARE THEIR PURPOSES?
Cookies are small text files stored on your device or web server by the websites you visit through your browsers. These small text files, containing your preferred language and other settings, help us remember your preferences on your next visit and assist us in making improvements to our services to enhance your experience on the site. This way, you can have a better and more personalized user experience on your next visit.
The main purposes of using cookies on our Internet Site are as follows:
3. TYPES OF COOKIES USED ON OUR INTERNET SITE 3.1. Session Cookies
Session cookies ensure the smooth operation of the internet site during your visit. They are used for purposes such as ensuring the security and continuity of our sites and your visits. Session cookies are temporary cookies and are deleted when you close your browser; they are not permanent.
3.2. Persistent Cookies
These cookies are used to remember your preferences and are stored on your device through browsers. Persistent cookies remain stored on your device even after you close your browser or restart your computer. These cookies are stored in your browser’s subfolders until deleted from your browser’s settings. Some types of persistent cookies can be used to provide personalized recommendations based on your usage purposes.
With persistent cookies, when you revisit our website with the same device, the website checks if a cookie created by our website exists on your device. If so, it is understood that you have visited the site before, and the content to be presented to you is determined accordingly, offering you a better service.
3.3. Mandatory/Technical Cookies
Mandatory cookies are essential for the proper functioning of the visited internet site. The purpose of these cookies is to provide necessary services by ensuring the operation of the site. For example, they allow access to secure sections of the internet site, use of its features, and navigation.
3.4. Analytical Cookies
These cookies gather information about how the website is used, the frequency and number of visits, and show how visitors navigate to the site. The purpose of using these cookies is to improve the operation of the site, increase its performance, and determine general trend directions. They do not contain data that can identify visitors. For example, they show the number of error messages displayed or the most visited pages.
3.5. Functional Cookies
Functional cookies remember the choices made by visitors within the site and recall them during the next visit. The purpose of these cookies is to provide ease of use to visitors. For example, they prevent the need to re-enter the user’s password on each page visited by the site user.
3.6. Targeting/Advertising Cookies
They measure the effectiveness of advertisements shown to visitors and calculate how many times ads are displayed. The purpose of these cookies is to present personalized advertisements to visitors based on their interests.
Similarly, they determine the specific interests of visitors’ navigation and present appropriate content. For example, they prevent the same advertisement from being shown again to the visitor in a short period.
4. HOW TO MANAGE COOKIE PREFERENCES?
To change your preferences regarding the use of cookies, block or delete cookies, you only need to change your browser settings.
Many browsers offer options to accept or reject cookies, only accept certain types of cookies, or receive notifications from the browser when a website requests to store cookies on your device.
Also, it is possible to delete previously saved cookies from your browser.
If you disable or reject cookies, you may need to manually adjust some preferences, and certain features and services on the website may not work properly as we will not be able to recognize and associate with your account. You can change your browser settings by clicking on the relevant link from the table below.
5. EFFECTIVE DATE OF THE INTERNET SITE PRIVACY POLICY
The Internet Site Privacy Policy is dated The effective date of the Policy will be updated if the entire Policy or specific sections are renewed. The Privacy Policy is published on the Organization’s website (www.socradar.com) and made accessible to relevant individuals upon request.
SOCRadar
Address: 651 N Broad St, Suite 205 Middletown, DE 19709 USA
Phone: +1 (571) 249-4598
Email: [email protected]
Website: www.socradar.com
