Threat intelligence enriched with External Attack Surface Management, Brand Protection, and Dark Web Radar.
Protect your business from the dangers lurking in the hidden corners of the internet.
Effective threat hunting and threat actor tracking with behavioral analytics.
Discover your assets with a hacker mindset.
Stay ahead of threat actors with actionable intelligence alerts.
Evaluate the security posture of your entire supply network.
Your guide in harnessing the full potential of our platform.
Hear SOCRadar’s impressive achievements from our clients.
Automate and operationalize your security operations.
Consulting and professional services for cybersecurity excellence.
Industry, sector, and region-based in-depth research.
Discover the heartbeat of cyberspace through a collection showcasing the latest incidents.
Discover how XTI empowers organizations to proactively identify, mitigate, and respond to evolving cyber threats.
Register for our live webinars, and watch our on-demand webinars instantly.
Dive deep into the world of cyber threats, advanced analysis techniques, and cutting-edge strategies.
Stay informed and up-to-date on the latest cybersecurity trends.
Explore SOCRadar’s learning experience to fuel your cybersecurity journey with insights that exceed industry standards.
We offer expert-led, and exclusive trainings to help you master the latest in cybersecurity, trusted by over 2,000 top companies.
Scan the dark web to prevent your leaks from turning into real risks.
Instantly access dark web findings about your organization’s assets.
Check if there is anything about you in SOCRadar’s ever-expanding breach database.
Track threat actors and groups by country or industry for effective follow-up.
Explore threat actors’ tactics, techniques, activities, and detailed profiles targeting your industry or region.
All-in-one next-generation tools for investigating everyday events like phishing, malware, account breach, etc.
Power your search with SOCRadar’s IOC Radar.
Let’s get to know each other better.
Broaden your market reach and increase ARR with SOCRadar Extended Threat Intelligence.
Get informed of our upcoming events.
Latest news about our platform, company, and what’s being said about us.
Begin an extraordinary journey in your professional path with SOCRadar.
We’d like to hear from you.
SOCRadar Training Series – Mastering AI in Cybersecurity From Theory to Practice
Resources
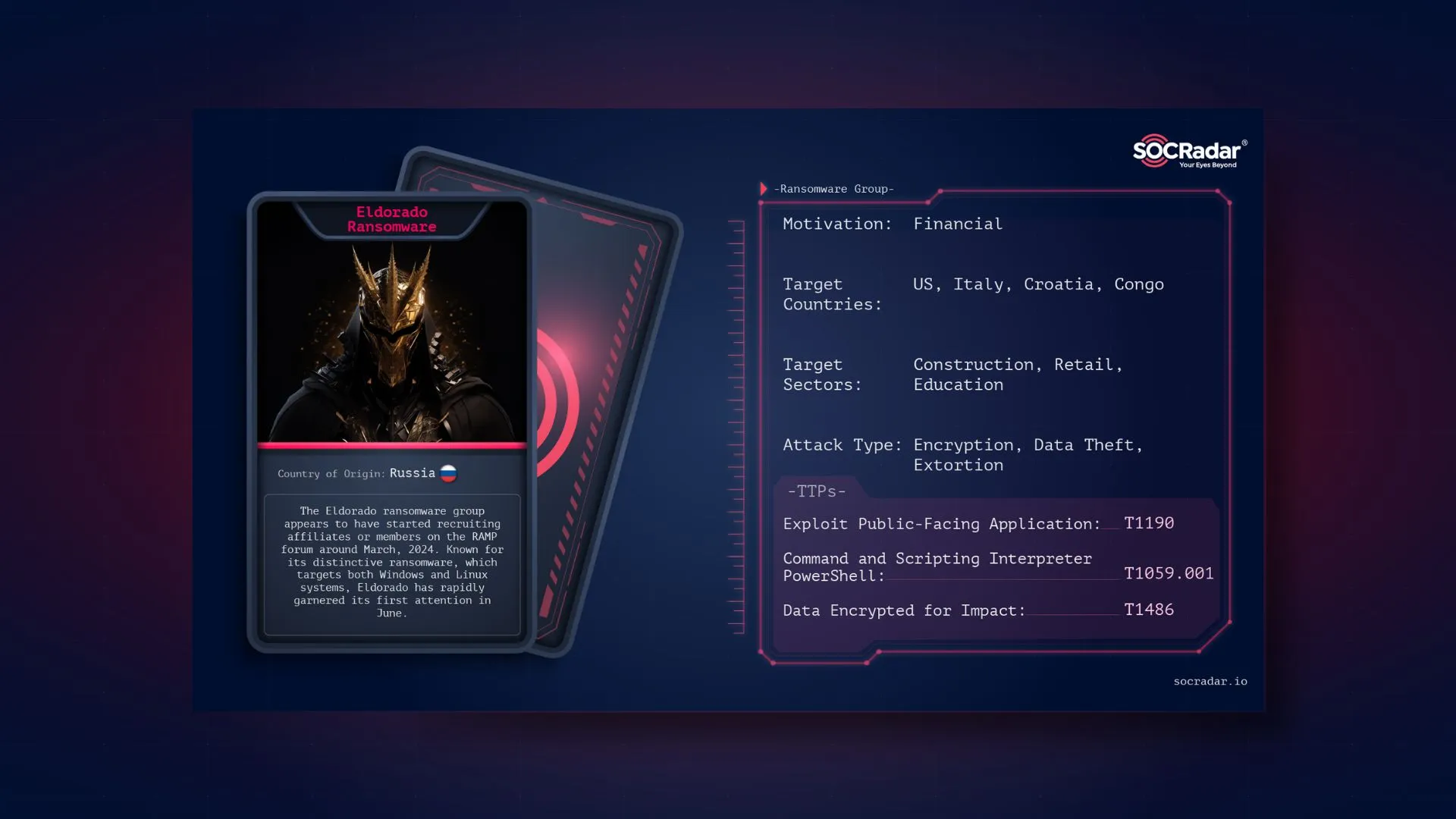
The Eldorado ransomware group, which reportedly emerged in March, operates a new Ransomware-as-a-Service (RaaS) platform featuring locker variants specifically designed for VMware ESXi and Windows systems. However, this group, which is thought to be of Russian origin, might have older ties.
This post delves into the origins, tactics, and impact of Eldorado, providing a comprehensive overview of this notorious cybercriminal organization.
Threat Actor Card for Eldorado Ransomware
El Dorado, often linked to the legend of a golden city or kingdom, originally referred to a 16th-century Muisca chief in Colombia known as El Hombre Dorado (“The Golden Man”) or El Rey Dorado (“The Golden King”). This chief covered himself in gold dust and submerged in Lake Guatavita as an initiation rite. Similarly, threat actors using this alias aim to make their own fortune.
A depiction of Eldorado Ransomware created with Bing AI
The Eldorado ransomware group appears to have started recruiting affiliates or members on the RAMP forum around March, 2024. Known for its distinctive ransomware, which targets both Windows and Linux systems, Eldorado has rapidly garnered its first attention in June. As a Ransomware-as-a-Service (RaaS) platform, it enables affiliates to use their ransomware toolkit to execute attacks, greatly expanding their reach and impact.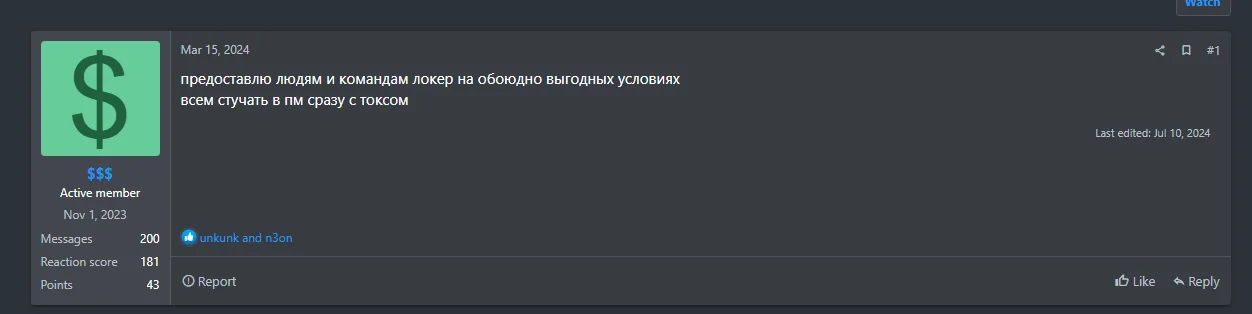
Post of the group’s possible owner on March 15, the Russian text as translated by Google: “I will provide people and teams with a locker on mutually beneficial terms, PM everyone immediately with tox”
The SOCRadar Dark Web team has been monitoring the group’s data leak site since it emerged in June. In an article published in early July, it was reported that the group’s activities were ongoing since at least March 2024. However, it is possible that the group has been active for a longer period than currently known in a different shape or form.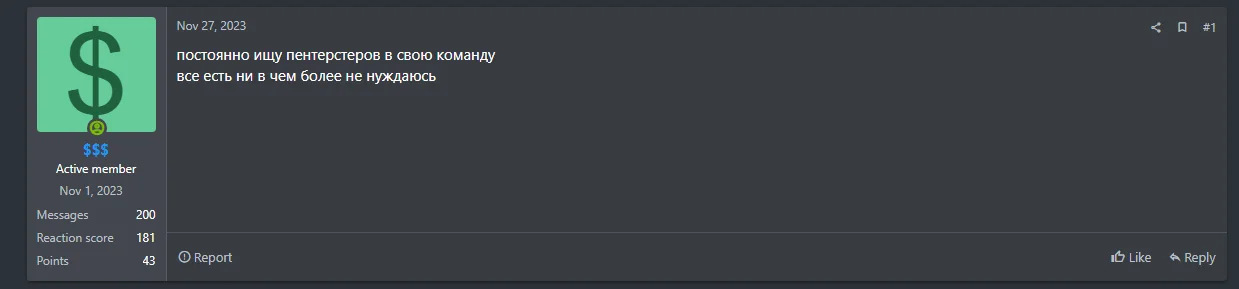
A post of the same threat actor in November, as translated by Google: “I’m constantly looking for pensters to join my team, I have everything, I don’t need anything more”
The threat actor with the pseudonym $$$ was looking for pen-testers to join his team on the Russian hacking forum called RAMP in November 2023. Such postings can be, and have been, early signals of a ransomware group.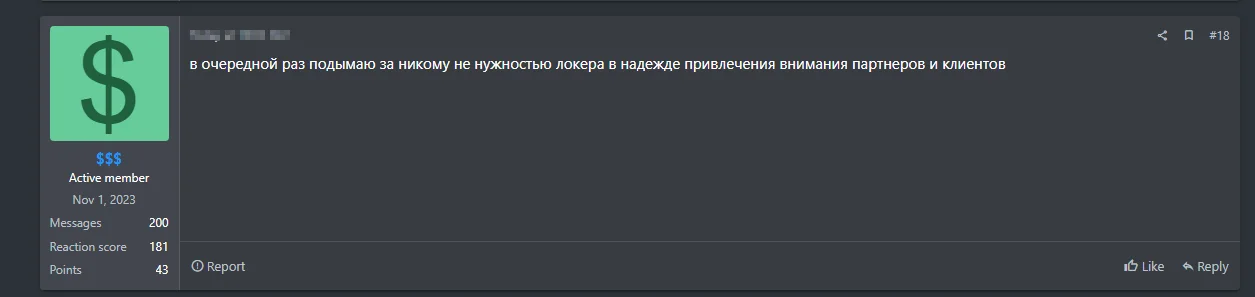
One of the latest post from the threat actor in 23 of July, as translated by Google: “Once again I’m raising a locker that no one needs in the hope of attracting the attention of partners and clients”
The ransomware group leader is still looking for affiliates in the same forum. The main problem of the group, which has not been active since June, seems to be the lack of affiliates and partners. So, let’s see what danger this group could pose if it can reach a wider affiliate network.
Although the exact strategy used by the group at the initial access point is unclear, it can be inferred that their primary access vector involves exploiting unpatched vulnerable systems, especially given that their known samples target VMware ESXi -a bare metal hypervisor, meaning it is installed directly on a physical server, allowing multiple virtual machines to run on the same hardware- servers. Additionally, the group likely seeks to obtain accesses such as Remote Desktop Protocol (RDP) access, and their search for pen-testers prior to the ransomware operation further support these hypotheses.
One of Eldorado’s notable strategies involves targeting VMware ESXi servers. These servers are critical in enterprise environments, often hosting numerous virtual machines. By exploiting vulnerabilities in outdated ESXi versions, Eldorado can deploy ransomware that encrypts virtual machines, causing significant disruption and demanding hefty ransoms for decryption keys.
Furthermore, Eldorado has samples that have capabilities to attack both Windows and Linux environments. This dual-targeting approach expands their potential attack surface and makes them a versatile threat to various organizations.
The group’s affiliate program’s details included a contact on the encrypted chat platform, TOX. The forum post, written in Russian, revealed that the ransomware was accompanied by a loader and that the attacker is still actively seeking team members for their operations.
This Russian-speaking operator primarily used a chat platform accessible via the Onion domain to communicate with victims. The ransomware’s control panel allows affiliates to generate ransomware samples by specifying parameters such as the name of the targeted network or company, the file name and text for the ransom note, and either the domain admin’s password or its hash.
Researchers obtained a copy of the Eldorado encryptor along with a user manual. The ransomware is available in four versions: esxi, esxi_64, win, and win_64.
Technically, Eldorado ransomware is written in Golang, known for its cross-platform capabilities. It supports both Windows and Linux operating systems.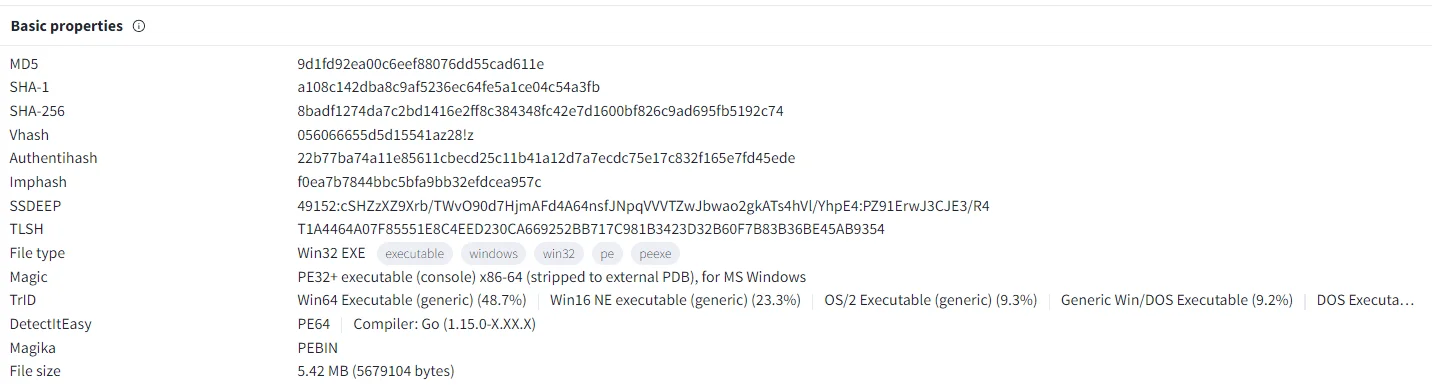
Basic properties of a known sample, written in Golang (VirusTotal)
According to researchers, the ransomware encrypts files using Chacha20 and RSA-OAEP. Each encrypted file is appended with a 32-byte key and 12-byte nonce, which are encrypted with RSA-OAEP and added to the end of the file.
The Windows version of Eldorado ransomware allows various command-line parameters to customize its operation, including options to specify directories for encryption, skip local files, define networks, and manage SMB credentials. It also includes a self-deletion mechanism, with an option to bypass this cleanup using the -keep flag. The Linux version is simpler, supporting only the -path argument, but uses the same encryption algorithms.
During execution, Eldorado ransomware logs its activities and communicates with the command and control server via WebSockets. To obscure its presence, it overwrites its own executable with random bytes before deleting it and removes shadow volume copies to prevent file recovery. This thorough approach to file encryption and system cleanup underscores the ransomware’s design to maximize disruption and complicate recovery efforts.
Similar to a classic ransomware operation, Eldorado ransomware leaves a text file titled “how to return or decrypt your files” in the Desktop and Documents folders. Interestingly, this ransom note is identical to one used by LostTrust ransomware, which has been inactive for some time.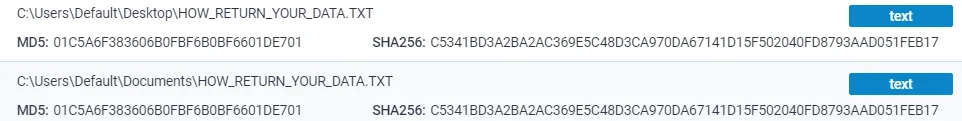
Dropped files of how to return your data (Any.run)
It’s believed that the LostTrust group was a spin-off from a ransomware operation called MetaEncryptor. This suggests a possible connection between these operations. It’s also worth noting that ransomware actors, many of whom are based in Russia, often share tactics and tools, sometimes even assisting each other, creating a legacy of shared methods.
LostTrust’s ransom note is identical to Eldorado’s
Another notable detail is that some Eldorado ransomware samples are detected by antivirus programs as Snatch malware. This may be due to its Golang codebase, but further investigation is needed. Additionally, when examining samples in open-source sources, it’s important to note that the infamous Eldorado Trojan, which shares the same name, can be confused with the ransomware samples used in this operation.
According to their data leak site (DLS), since its emergence, Eldorado ransomware has impacted 15 companies across various countries and industries. The majority of these attacks, 11 out of 15, have been in the United States. Italy has seen two attacks, while the Republic of the Congo and Croatia have each experienced one attack.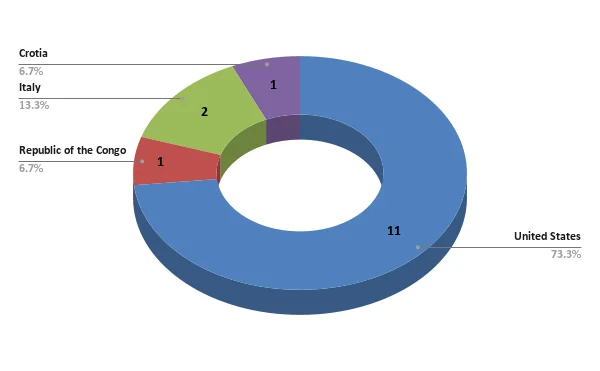
Targeted countries so far
The ransomware group’s most targeted sectors include Construction with three attacks, Education with two attacks, and Manufacturing, Information, Professional, Scientific & Technical Services, Telecommunications, Retail, Administrative and Support Services, Business Services, Amusement & Recreation Services, Administrative Services, and Transportation, each with one attack.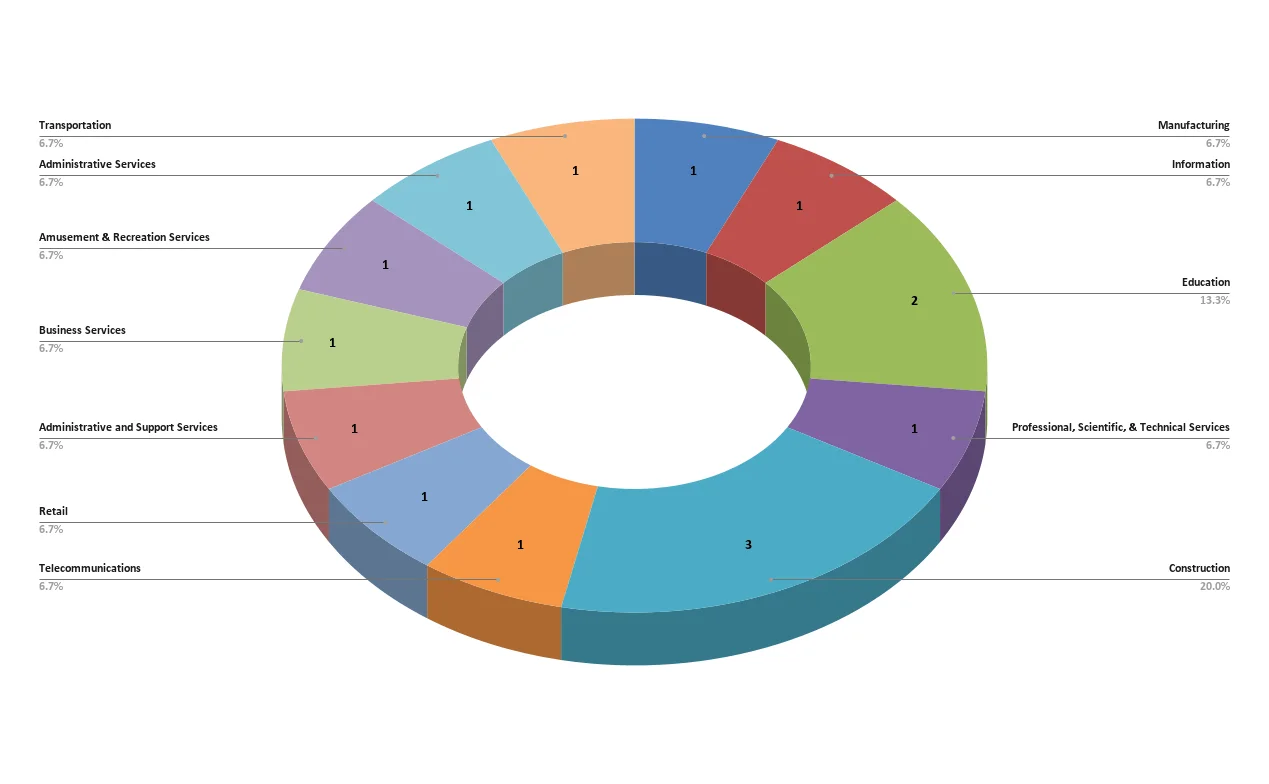
Targeted industries so far
As cyber threats continue to evolve, organizations must adopt a multifaceted approach to cybersecurity, especially in defending against ransomware attacks like Eldorado. Leveraging advanced security tools and implementing proactive strategies are imperative in fortifying digital defenses.
Anti-Malware Solutions: Implementing advanced anti-malware software is essential in combating Eldorado ransomware. These tools use signature-based detection, heuristic analysis, and machine learning algorithms to identify and block known and emerging ransomware variants. Coupled with Endpoint Detection and Response (EDR) solutions, organizations can enhance real-time threat detection and response capabilities.
Security Audits and Vulnerability Management: Conducting routine security audits and vulnerability assessments is critical to identifying and addressing potential security gaps within an organization’s infrastructure. By systematically evaluating network configurations, system settings, and application vulnerabilities, organizations can proactively remediate weaknesses exploited by Eldorado ransomware attackers.
Authentication and Access Controls: Enforcing strong authentication mechanisms like Multi-Factor Authentication (MFA) and implementing stringent access controls significantly enhances user account security and mitigates the risk of unauthorized access. This adds an extra layer of protection against Eldorado ransomware attacks targeting user credentials.
Comprehensive Backup and Disaster Recovery Planning: Developing a robust Backup and Disaster Recovery (BDR) plan is essential in mitigating the impact of Eldorado ransomware attacks and ensuring business continuity. Regular backup schedules for critical data, both onsite and offsite, along with backup testing and data recovery drills, validate the effectiveness of the BDR plan and ensure timely restoration of operations in case of an attack.
Dark Web Monitoring: Utilize SOCRadar’s Advanced Dark Web Monitoring to track unauthorized data transfers, detect PII exposures, and monitor dark web channels for potential threats related to Eldorado ransomware.
For further information about protection against ransomware, also check out our blog post titled “How to Detect & Prevent Ransomware Attacks (2024 CISO Edition).”
Understanding the tactics and strategies of ransomware groups like Eldorado is crucial for organizations looking to bolster their cybersecurity defenses. Implementing robust mitigation measures and staying vigilant are key steps in combating these threats effectively.
SOCRadar’s Attack Surface Management includes a specialized Ransomware Check function designed to help organizations protect against ransomware attacks, including those orchestrated by groups like Eldorado. Our platform empowers you to proactively monitor potential attack vectors, detect suspicious activities, and take preemptive actions to safeguard your digital assets.
SOCRadar Attack Surface Management with ransomware check function
By leveraging SOCRadar’s intelligence-driven solutions, you can gain insights into threat actors’ methods and vulnerabilities, enabling you to fortify your cybersecurity posture. Our continuous monitoring and timely alerts ensure that you stay ahead of potential threats, allowing for swift responses and enhanced overall defense against ransomware and other cyber threats.
Integrating SOCRadar into your cybersecurity framework adds an additional layer of protection, helping you mitigate the risks posed by ransomware groups like Eldorado and ensuring the resilience of your organization’s security defenses.
In summary, the Eldorado ransomware group, emerging in March 2024(?), has quickly become a significant threat in the cyber landscape. Operating as a Ransomware-as-a-Service (RaaS) platform, Eldorado targets both VMware ESXi and Windows systems, expanding its reach and impact. Its technical sophistication, use of Golang, and ability to encrypt files with Chacha20 and RSA-OAEP highlight its capabilities.
The group’s recruitment efforts on forums and its potential connections to other ransomware groups like LostTrust and MetaEncryptor suggest a deeper, collaborative underground network. To combat this evolving threat, organizations must adopt advanced cybersecurity measures, including anti-malware solutions, regular security audits, strong authentication protocols, comprehensive backup plans, and dark web monitoring.
Below are the known and possible TTPs of Eldorado Ransomware operation, due to its being a RaaS the TTPs of the threat actors may expand and shrink inline with their capabilities.
For the IoCs please refer to SOCRadar Platform’s Ransomware Intelligence.
Subscribe to our newsletter and stay updated on the latest insights!
PROTECTION OF PERSONAL DATA COOKIE POLICY FOR THE INTERNET SITE
Protecting your personal data is one of the core principles of our organization, SOCRadar, which operates the internet site (www.socradar.com). This Cookie Usage Policy (“Policy”) explains the types of cookies used and the conditions under which they are used to all website visitors and users.
Cookies are small text files stored on your computer or mobile device by the websites you visit.
Cookies are commonly used to provide you with a personalized experience while using a website, enhance the services offered, and improve your overall browsing experience, contributing to ease of use while navigating a website. If you prefer not to use cookies, you can delete or block them through your browser settings. However, please be aware that this may affect your usage of our website. Unless you change your cookie settings in your browser, we will assume that you accept the use of cookies on this site.
1. WHAT KIND OF DATA IS PROCESSED IN COOKIES?
Cookies on websites collect data related to your browsing and usage preferences on the device you use to visit the site, depending on their type. This data includes information about the pages you access, the services and products you explore, your preferred language choice, and other preferences.
2. WHAT ARE COOKIES AND WHAT ARE THEIR PURPOSES?
Cookies are small text files stored on your device or web server by the websites you visit through your browsers. These small text files, containing your preferred language and other settings, help us remember your preferences on your next visit and assist us in making improvements to our services to enhance your experience on the site. This way, you can have a better and more personalized user experience on your next visit.
The main purposes of using cookies on our Internet Site are as follows:
3. TYPES OF COOKIES USED ON OUR INTERNET SITE 3.1. Session Cookies
Session cookies ensure the smooth operation of the internet site during your visit. They are used for purposes such as ensuring the security and continuity of our sites and your visits. Session cookies are temporary cookies and are deleted when you close your browser; they are not permanent.
3.2. Persistent Cookies
These cookies are used to remember your preferences and are stored on your device through browsers. Persistent cookies remain stored on your device even after you close your browser or restart your computer. These cookies are stored in your browser’s subfolders until deleted from your browser’s settings. Some types of persistent cookies can be used to provide personalized recommendations based on your usage purposes.
With persistent cookies, when you revisit our website with the same device, the website checks if a cookie created by our website exists on your device. If so, it is understood that you have visited the site before, and the content to be presented to you is determined accordingly, offering you a better service.
3.3. Mandatory/Technical Cookies
Mandatory cookies are essential for the proper functioning of the visited internet site. The purpose of these cookies is to provide necessary services by ensuring the operation of the site. For example, they allow access to secure sections of the internet site, use of its features, and navigation.
3.4. Analytical Cookies
These cookies gather information about how the website is used, the frequency and number of visits, and show how visitors navigate to the site. The purpose of using these cookies is to improve the operation of the site, increase its performance, and determine general trend directions. They do not contain data that can identify visitors. For example, they show the number of error messages displayed or the most visited pages.
3.5. Functional Cookies
Functional cookies remember the choices made by visitors within the site and recall them during the next visit. The purpose of these cookies is to provide ease of use to visitors. For example, they prevent the need to re-enter the user’s password on each page visited by the site user.
3.6. Targeting/Advertising Cookies
They measure the effectiveness of advertisements shown to visitors and calculate how many times ads are displayed. The purpose of these cookies is to present personalized advertisements to visitors based on their interests.
Similarly, they determine the specific interests of visitors’ navigation and present appropriate content. For example, they prevent the same advertisement from being shown again to the visitor in a short period.
4. HOW TO MANAGE COOKIE PREFERENCES?
To change your preferences regarding the use of cookies, block or delete cookies, you only need to change your browser settings.
Many browsers offer options to accept or reject cookies, only accept certain types of cookies, or receive notifications from the browser when a website requests to store cookies on your device.
Also, it is possible to delete previously saved cookies from your browser.
If you disable or reject cookies, you may need to manually adjust some preferences, and certain features and services on the website may not work properly as we will not be able to recognize and associate with your account. You can change your browser settings by clicking on the relevant link from the table below.
5. EFFECTIVE DATE OF THE INTERNET SITE PRIVACY POLICY
The Internet Site Privacy Policy is dated The effective date of the Policy will be updated if the entire Policy or specific sections are renewed. The Privacy Policy is published on the Organization’s website (www.socradar.com) and made accessible to relevant individuals upon request.
SOCRadar
Address: 651 N Broad St, Suite 205 Middletown, DE 19709 USA
Phone: +1 (571) 249-4598
Email: [email protected]
Website: www.socradar.com
