
Threat intelligence enriched with External Attack Surface Management, Brand Protection, and Dark Web Radar.
Protect your business from the dangers lurking in the hidden corners of the internet.
Effective threat hunting and threat actor tracking with behavioral analytics.
Discover your assets with a hacker mindset.
Stay ahead of threat actors with actionable intelligence alerts.
Evaluate the security posture of your entire supply network.
Your guide in harnessing the full potential of our platform.
Hear SOCRadar’s impressive achievements from our clients.
Automate and operationalize your security operations.
Consulting and professional services for cybersecurity excellence.
Industry, sector, and region-based in-depth research.
Discover the heartbeat of cyberspace through a collection showcasing the latest incidents.
Discover how XTI empowers organizations to proactively identify, mitigate, and respond to evolving cyber threats.
Register for our live webinars, and watch our on-demand webinars instantly.
Dive deep into the world of cyber threats, advanced analysis techniques, and cutting-edge strategies.
Stay informed and up-to-date on the latest cybersecurity trends.
Explore SOCRadar’s learning experience to fuel your cybersecurity journey with insights that exceed industry standards.
We offer expert-led, and exclusive trainings to help you master the latest in cybersecurity, trusted by over 2,000 top companies.
Scan the dark web to prevent your leaks from turning into real risks.
Instantly access dark web findings about your organization’s assets.
Check if there is anything about you in SOCRadar’s ever-expanding breach database.
Track threat actors and groups by country or industry for effective follow-up.
Explore threat actors’ tactics, techniques, activities, and detailed profiles targeting your industry or region.
All-in-one next-generation tools for investigating everyday events like phishing, malware, account breach, etc.
Power your search with SOCRadar’s IOC Radar.
Let’s get to know each other better.
Broaden your market reach and increase ARR with SOCRadar Extended Threat Intelligence.
Get informed of our upcoming events.
Latest news about our platform, company, and what’s being said about us.
Begin an extraordinary journey in your professional path with SOCRadar.
We’d like to hear from you.
SOCRadar Training Series – Mastering AI in Cybersecurity From Theory to Practice
Resources
IntelBroker, a notorious figure known for orchestrating high-profile cyberattacks, operates within BreachForums. Specializing in identifying and selling access to compromised systems, sensitive data leaks, and possibly extortion, IntelBroker facilitates various malicious activities.
Most known profile picture of IntelBroker
BreachForums, IntelBroker’s long-time base, was recently taken down once again in an operation. This led to the revival of a diminished, Frankenstein-like version that lost some of its key members. The struggling forum is no longer managed by ShinyHunters, while the USDoD is seeking to establish its own platform. Despite these changes, the forum’s standout member, IntelBroker, remains active.
Possibly the most known member of BreachForums, also known with ransomware attempts under the name Endurance Ransomware. IntelBroker we know today emerged in late 2022 and gained notoriety in early 2023 after allegedly breaching the Weee Grocery Service.
Other notable breaches attributed to IntelBroker include Europol, Autotrader, Volvo, Hilton Hotels, and AT&T, apart from the more recent incidents. Although not every breach can be verified to the same extent, many incidents caused by IntelBroker were confirmed leaks.
In 2023, IntelBroker became a member of CyberNiggers, a racist cybercrime group active on BreachForums. IntelBroker was just a member within the group, yet the group’s most significant attacks were orchestrated by IntelBroker during its tenure. The other group members also continued to execute similar attacks.
Statements in leak posts from group members suggested mutual assistance, although the extent of these collaborations remains unclear. Nevertheless, IntelBroker managed to preserve its distinctive identity and achieved notoriety, surpassing the group’s.
Threat actor card for CyberNiggers, Dark Web Profile: CyberNiggers
CyberNiggers’ lair, BreachForums is a complicated platform. It has been revived multiple times, firstly following the arrests of its administrator “pompompurin” but continued to be operational. The forum once again experienced a similar fate but now still remains operational.
For now, CyberNiggers seems to no longer exist, but IntelBroker continues to publish its activities on this forum, gain contacts, and collaborate with other actors.
In the past, DoD Cyber Crime Center suggested that Endurance Ransomware might be an Iranian state entity, which is IntelBroker’s ransomware strain’s name, noting similarities between the malware it used and the infamous Shamoon wiping tool. However, IntelBroker denies these allegations, asserting independence and claiming to be a single individual from Serbia.
Current profile picture of IntelBroker
In a YouTube interview, IntelBroker stated it is from Serbia but resides in Russia for operational safety. This context may shed light on IntelBroker’s objectives and political stance.
Recent discussions about IntelBroker have long shifted away from claims involving Iran, yet similarities between the Tactics, Techniques, and Procedures (TTPs) of Iranian actors and those of contemporary hacker collectives and hacktivist groups based in Russia are evident. This could suggest a potential overlap in cyber capabilities and strategies between the two regions, akin to broader geopolitical dynamics such as Iran’s drone sales to Russia.
In conclusion, allegations around IntelBroker’s identity persist. Whether Serbian or not, it’s conceivable that IntelBroker operates independently, possibly utilizing Iranian malware variants previously. However, the actor’s sophisticated attacks on high-profile targets, particularly within the US defense sector, raise questions about potential state sponsorship or collaboration with state entities.
Even if we do not have an incident response study, IntelBroker’s modus operandi can be estimated from its known techniques and the content of the leaked data.
IntelBroker possibly employs a multifaceted approach to cyberattacks characterized by strategic initial access brokering and data exfiltration tactics. Operating within the recently revived BreachForums, IntelBroker is pivotal in identifying and monetizing access to compromised systems, facilitating a range of malicious activities.
IntelBroker typically begins by attempting to sell the access he has acquired. If unsuccessful, it likely resorts to conducting its own infiltration efforts to steal data. However, this approach may have shifted from solely selling access to initiating its own data breaches over time. These days, the actor posts samples of data available for sale on the forum.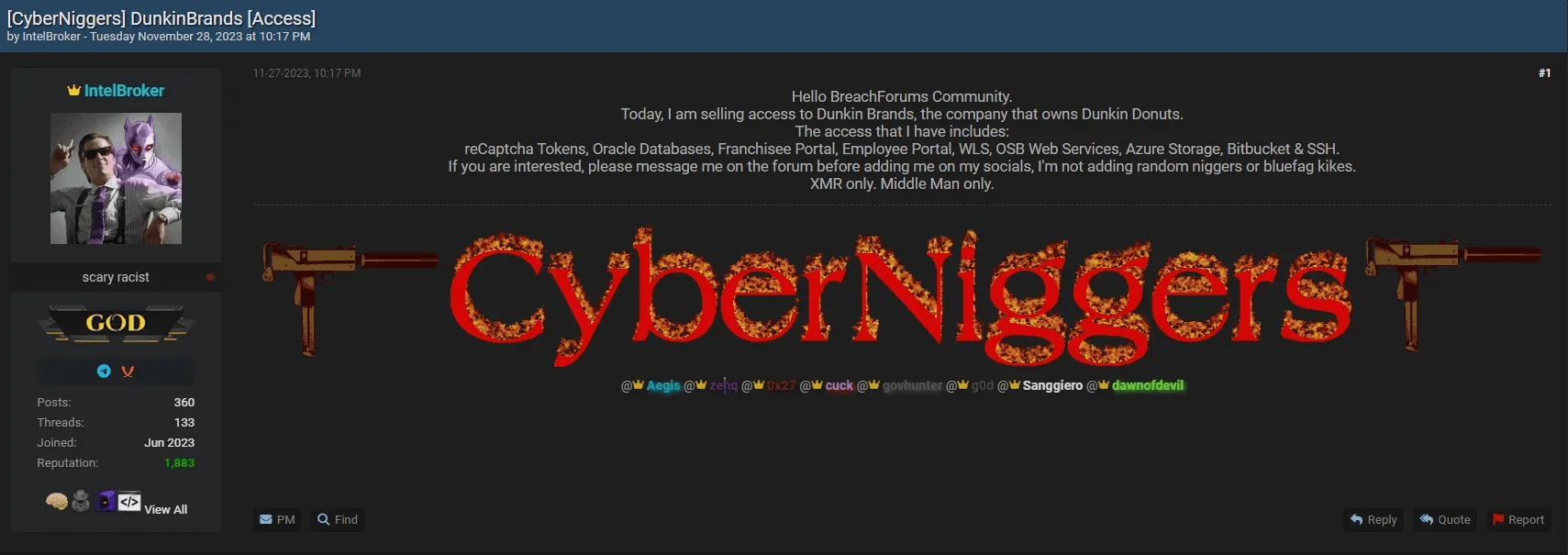
An access sale by IntelBroker
According to its statements across different posts, its modus operandi should encompass several techniques, like leveraging exploits targeting vulnerabilities in public-facing applications to gain initial access to targeted organizations.
Additionally, purchasing initial access leads from other actors who share similar tactics, techniques, procedures, and objectives is possible. Acquiring credentials through stealer logs and leveraging Personally Identifiable Information (PII) from these logs for impersonation attacks or insider threats are also common initial access vectors employed by such actors.
For instance, the threat actor USDoD, previously active on BreachForums, mentioned in an interview that its attack vector included these methods.
As can be interpreted by the content of IntelBroker’s leaks, once inside, IntelBroker executes unauthorized commands and manipulates accounts to establish persistent access, ensuring prolonged infiltration and exploitation capabilities.
Furthermore, IntelBroker is adept at escalating privileges within compromised networks as it publishes source codes from internal tools, using techniques to gain higher-level access and circumvent security measures. To evade detection, it employs tactics like obfuscating malicious files and information, making it challenging for security defenses to detect and mitigate its activities effectively.
Credential dumping might be another integral aspect of IntelBroker’s methodology, allowing him to harvest and utilize compromised credentials to expand its access within networks. Its operations include the comprehensive discovery of files and directories within compromised systems, such as alleged sensitive military files associated with DARPA.
Therefore, IntelBroker’s activities could extend beyond initial access and persistence to include lateral movement across networks using valid accounts, enabling him to explore and compromise diverse organizational targets. Its approach culminates in the collection and exfiltration of sensitive data via command and control channels, ensuring the extraction of valuable information from compromised environments.
IntelBroker, which claimed to be developing the Endurance Ransomware strain in a post in 2023, currently has no visible connection with ransomware. Notably, BreachForums banned ransomware-related topics during operations against ransomware groups such as ALPHV and LockBit. In this context, it appears that extortion is now preferred over ransomware in the general cybercrime landscape, and IntelBroker is not currently involved in ransomware activities.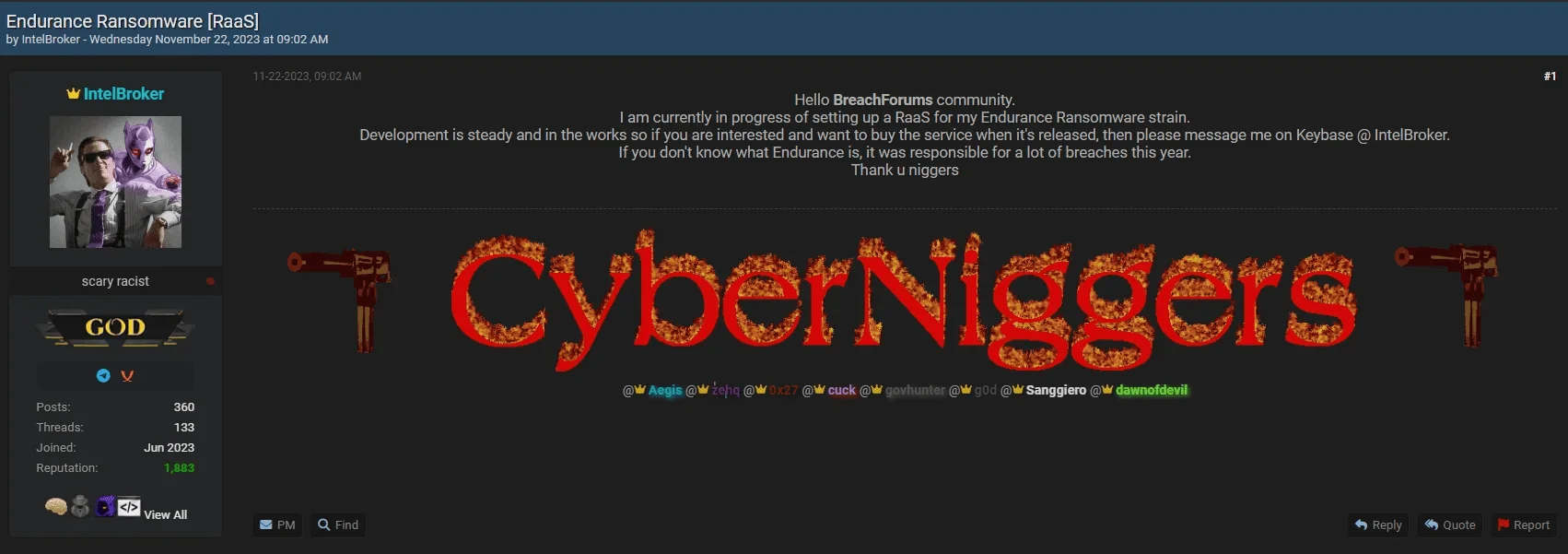
About the Endurance Ransomware
IntelBroker’s activities are predominantly motivated by financial gain, as indicated by its sale of access to crucial data and systems. However, its actions sometimes intersect with broader geopolitical considerations, especially when targeting entities in NATO-aligned nations such as the United States. This dual emphasis on financial incentives and occasional geopolitical messaging highlights the complex nature of IntelBroker.
When examining the current posts on BreachForums, we observe at least 82 instances of leaks, access sales, and vulnerability sales. Some older posts are not accessible. Furthermore, some of its posts mention access sales for over 400 companies, and one post about an alleged attack on the US energy sector lists 27 companies. Therefore, it is possible to consider hundreds of companies are targeted, but in the analysis below, we will focus on victim analysis through unique posts.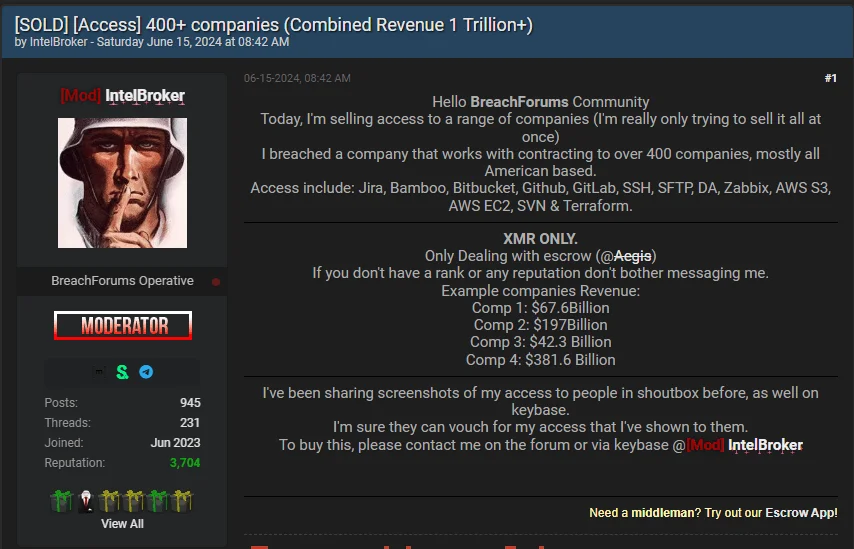
Now a moderator, IntelBroker’s access sales for over 400 companies
IntelBroker is known for targeting a wide range of industries across multiple countries. The following analysis breaks down the patterns and preferences exhibited by IntelBroker based on its alleged victims on unique posts.
IntelBroker, targets a diverse array of industries across multiple countries, displaying a strategic focus and methodical approach in victim selection. Geographically, their operations span continents, with notable concentrations in key regions. Predominantly, the United States serves as a primary target, leveraging its data-rich environments and critical infrastructure. Additionally, IntelBroker has shown significant interest in India, drawn by its rapid digital expansion, alongside frequent incursions into European nations such as the United Kingdom and France. Moreover, a politically motivated approach should also be mentioned.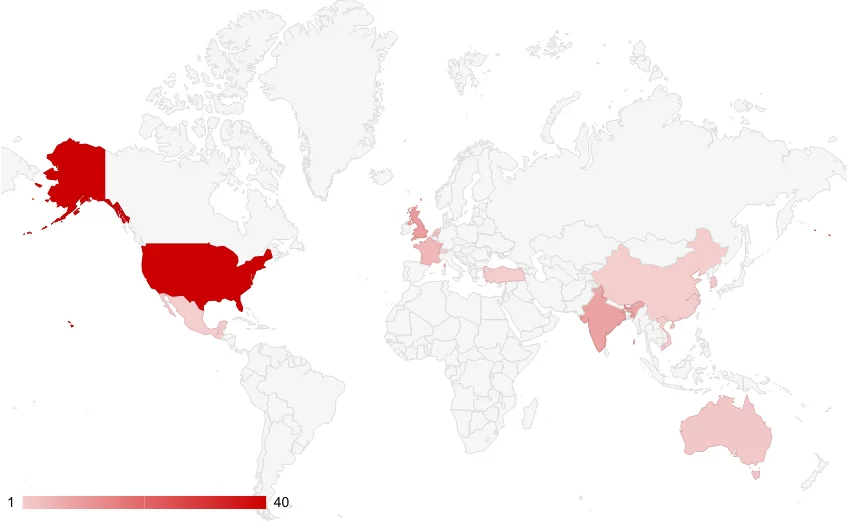
Targeted countries according to organizations’ headquarters
In terms of industry focus, IntelBroker exhibits a broad scope, targeting sectors with substantial data assets. They display no discernible bias against any particular industry but concentrate their efforts where data value is perceived to be high. This includes Information Technology and Telecommunications, Healthcare, Financial Services, Government and Public Administration, Education, Retail and E-Commerce, Transportation and Logistics, Professional Services, and Manufacturing sectors.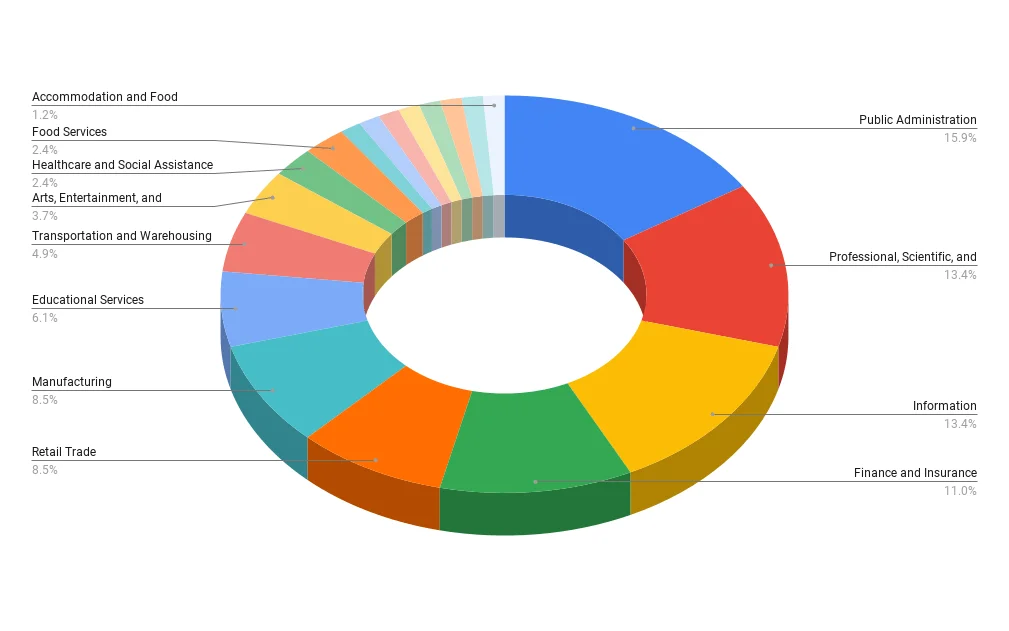
Industries targeted by IntelBroker according to the current posts in BreachForums
IntelBroker demonstrates a clear preference for targeting entities related to national security. Notable incidents include data leaks from the State and Homeland Security Departments, classified DARPA documents, and offers of access to a system named “US Army Dashboard.” It also targeted a cybersecurity defense contractor to exfiltrate classified NSA documents related to Five Eyes communications and Europol. These attacks on various government entities suggest a motivation to undermine the US government, evidenced by leaking flight logs from the US Transportation Department, breaching Los Angeles airport systems, compromising the US Citizenship and Immigration Services, and exposing Congress members’ personal information.
In addition to government entities, IntelBroker also targets critical infrastructure sectors, particularly IT and telecommunications. It has allegedly stolen credentials from HPE, AT&T, and Verizon and allegedly breached Zcaler. IntelBroker has also targeted e-commerce platforms like Weee! and PandaBuy, allegedly extracted credentials from financial institutions like Barclays and HSBC, attacked companies like Accor and Home Depot, and leaked thousands of records from Facebook Marketplace. This breadth of activity underscores their sophisticated and wide-reaching approach to cyber attacks.
Weee Grocery Service: IntelBroker claimed responsibility for a significant data breach involving Weee Grocery Service, a popular online grocery platform. This breach affected approximately 11 million users, raising serious concerns about the exposure of personal and financial information. The importance of this incident lies in the fact that it was one of IntelBroker’s first high-profile attacks, marking the beginning of widespread attention to its activities.
Los Angeles International Airport: IntelBroker infiltrated a database containing 2.5 million records, including full names, CPA numbers, company names, plane model numbers, aircraft tail numbers, and 1.9 million emails. This breach was carried out through an attack on the airport’s vulnerable customer relationship management system.
Acuity: IntelBroker accessed data from the US Immigration and Customs Enforcement and US Citizenship and Immigration Services by exploiting a critical GitHub zero-day vulnerability. This breach compromised the personal information of over 100,000 US citizens and allegedly included sensitive documents related to the Five Eyes alliance’s investigative methods and the ongoing Russia-Ukraine war.
Other breaches linked to IntelBroker involve high-profile targets such as General Electric, Hewlett Packard Enterprise, AT&T, and Verizon.
Europol: the European Union’s law enforcement agency, allegedly fell victim to a data breach on May 10, 2024, exposing highly sensitive information and classified data. The alleged breach claimed by IntelBroker. The allegedly compromised data included many sensitive materials, ranging from alliance employee information to FOUO source code, PDFs, documents for reconnaissance, and operational guidelines. In the same week, IntelBroker claimed that it had also breached Zscaler.
Europol data breach claim
Apple and AMD: One of its most recent attacks targeted two tech giants. IntelBroker claimed to have breached Apple’s internal site on June 19, 2024. It claimed exposure of internal tools such as AppleConnect-SSO, Apple-HWE-Confluence-Advanced, and AppleMacroPlugin. Furthermore, on June 18, 2024, IntelBroker purportedly breached AMD’s database, exposing a wide range of data, including future product details, spec sheets, customer databases, property files, ROMs, source code, firmware, finances, and extensive employee information (User ID, full names, job functions, phone numbers, emails, etc.).
The post about Apple Internal Tools Breach
Below are the most possible TTPs for IntelBroker’s activities. However, it should be reminded again that this is not an incident response and investigation study, but has been prepared based on the content of the alleged activities and data.
IntelBroker, operating within the shadows of BreachForums, remains a formidable presence in the cyber threat landscape despite recent disruptions to the forum. Specializing in exploiting vulnerabilities across a wide range of industries and geographies, IntelBroker’s activities span from high-profile data breaches at companies like Weee Grocery Service and AT&T to infiltrating sensitive government agencies and critical infrastructure. Notably, its recent claims of breaching Apple and AMD highlight its ongoing capability to target major technology firms and extract valuable intellectual property.
Response to breaches, confirmation of claims, and building strong cybersecurity defenses are crucial for reducing the impact of cyber threats. In today’s cybersecurity environment, it’s essential to stay alert and adaptable and work together to protect critical infrastructure, national security, and personal data.
SOCRadar Dark Web Monitoring offers comprehensive monitoring across the web’s different layers—surface, deep, and dark web. SOCRadar allows organizations to detect and tackle threats effectively. With our expertise in reconnaissance and threat analysis, we provide practical insights to strengthen your proactive security efforts. Integrating automated cyber intelligence with expert analysts empowers Security Operations Center (SOC) teams to handle threats proactively, extending their defense capabilities.
SOCRadar Dark Web Monitoring
Subscribe to our newsletter and stay updated on the latest insights!
PROTECTION OF PERSONAL DATA COOKIE POLICY FOR THE INTERNET SITE
Protecting your personal data is one of the core principles of our organization, SOCRadar, which operates the internet site (www.socradar.com). This Cookie Usage Policy (“Policy”) explains the types of cookies used and the conditions under which they are used to all website visitors and users.
Cookies are small text files stored on your computer or mobile device by the websites you visit.
Cookies are commonly used to provide you with a personalized experience while using a website, enhance the services offered, and improve your overall browsing experience, contributing to ease of use while navigating a website. If you prefer not to use cookies, you can delete or block them through your browser settings. However, please be aware that this may affect your usage of our website. Unless you change your cookie settings in your browser, we will assume that you accept the use of cookies on this site.
1. WHAT KIND OF DATA IS PROCESSED IN COOKIES?
Cookies on websites collect data related to your browsing and usage preferences on the device you use to visit the site, depending on their type. This data includes information about the pages you access, the services and products you explore, your preferred language choice, and other preferences.
2. WHAT ARE COOKIES AND WHAT ARE THEIR PURPOSES?
Cookies are small text files stored on your device or web server by the websites you visit through your browsers. These small text files, containing your preferred language and other settings, help us remember your preferences on your next visit and assist us in making improvements to our services to enhance your experience on the site. This way, you can have a better and more personalized user experience on your next visit.
The main purposes of using cookies on our Internet Site are as follows:
3. TYPES OF COOKIES USED ON OUR INTERNET SITE 3.1. Session Cookies
Session cookies ensure the smooth operation of the internet site during your visit. They are used for purposes such as ensuring the security and continuity of our sites and your visits. Session cookies are temporary cookies and are deleted when you close your browser; they are not permanent.
3.2. Persistent Cookies
These cookies are used to remember your preferences and are stored on your device through browsers. Persistent cookies remain stored on your device even after you close your browser or restart your computer. These cookies are stored in your browser’s subfolders until deleted from your browser’s settings. Some types of persistent cookies can be used to provide personalized recommendations based on your usage purposes.
With persistent cookies, when you revisit our website with the same device, the website checks if a cookie created by our website exists on your device. If so, it is understood that you have visited the site before, and the content to be presented to you is determined accordingly, offering you a better service.
3.3. Mandatory/Technical Cookies
Mandatory cookies are essential for the proper functioning of the visited internet site. The purpose of these cookies is to provide necessary services by ensuring the operation of the site. For example, they allow access to secure sections of the internet site, use of its features, and navigation.
3.4. Analytical Cookies
These cookies gather information about how the website is used, the frequency and number of visits, and show how visitors navigate to the site. The purpose of using these cookies is to improve the operation of the site, increase its performance, and determine general trend directions. They do not contain data that can identify visitors. For example, they show the number of error messages displayed or the most visited pages.
3.5. Functional Cookies
Functional cookies remember the choices made by visitors within the site and recall them during the next visit. The purpose of these cookies is to provide ease of use to visitors. For example, they prevent the need to re-enter the user’s password on each page visited by the site user.
3.6. Targeting/Advertising Cookies
They measure the effectiveness of advertisements shown to visitors and calculate how many times ads are displayed. The purpose of these cookies is to present personalized advertisements to visitors based on their interests.
Similarly, they determine the specific interests of visitors’ navigation and present appropriate content. For example, they prevent the same advertisement from being shown again to the visitor in a short period.
4. HOW TO MANAGE COOKIE PREFERENCES?
To change your preferences regarding the use of cookies, block or delete cookies, you only need to change your browser settings.
Many browsers offer options to accept or reject cookies, only accept certain types of cookies, or receive notifications from the browser when a website requests to store cookies on your device.
Also, it is possible to delete previously saved cookies from your browser.
If you disable or reject cookies, you may need to manually adjust some preferences, and certain features and services on the website may not work properly as we will not be able to recognize and associate with your account. You can change your browser settings by clicking on the relevant link from the table below.
5. EFFECTIVE DATE OF THE INTERNET SITE PRIVACY POLICY
The Internet Site Privacy Policy is dated The effective date of the Policy will be updated if the entire Policy or specific sections are renewed. The Privacy Policy is published on the Organization’s website (www.socradar.com) and made accessible to relevant individuals upon request.
SOCRadar
Address: 651 N Broad St, Suite 205 Middletown, DE 19709 USA
Phone: +1 (571) 249-4598
Email: [email protected]
Website: www.socradar.com
